Dynamic Patterns of Terrorist Networks
Military / Coalition Issue
Terrorist networks have a trade-off to consider between efficiency (of communication) vs security (to disruption) and need to “manage” this balance. This can be detected by network analysis if data is available. By sharing known data about terrorist organisations and operatives, can awareness be achieved, and insight into potential impending attacks?
Core idea and key achievements
By applying analytics to available terrorist network data for 11 attack events, we identified that these networks showed increased connectivity as the attack year approached, and substantial decreased connectivity after the attack (due to network disruption by law enforcement).
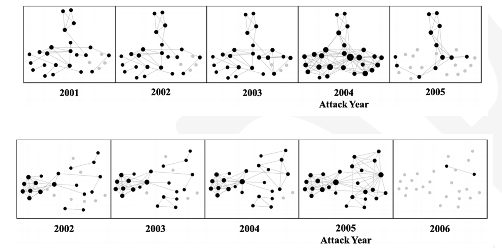
We used various descriptive network measures including Separable Temporal Exponential Random Graph Models (STERGMs) to measure network density as the basis for this analytics.
Implications for Defence
Our findings have the potential to inform counterterrorism efforts by suggesting which actors make the most influential targets for law enforcement. We discuss how these strategies should vary as extremist networks evolve over time. This could be used in a number of settings: e.g., to help predict group activities and attacks, to determine where costly resources such as detailed monitoring should be applied. Other behaviours may be observed for long-running terrorist groups rather than attack-focused networks that seek to perpetrate a single event.
Readiness & alternative Defence uses
This work is technology readiness level (TRL) 1/2. For the available data this technique has shown strong predictive potential for attack events, based on increased connectivity as the event nears. However, the data was limited and may have been subject to biases (e.g., collection bias). To take the work forward it would be valuable to apply this to broader terrorist network data, which is not publicly available.
The same tension between security and efficiency may apply in other non-terrorism settings and the STERGM method may be useful in calibrating the performance over time of other networks.
Resources and references
- McMillan, Cassie, Diane Felmlee, and Dave Braines. “Dynamic patterns of terrorist networks: Efficiency and security in the evolution of eleven islamic extremist attack networks.” Journal of quantitative criminology 36, no. 3 (2020): 559-581.
Organisations
Penn State, IBM UK